|
Other Interesting Stories...
|
Get ready for more attacks on big retail Point-of-Sale checkout equipment
HP's 2015 Cyber Risk Report is out, and the forecast is for more of the same (e.g. Expect more news like the Target, Staples, Home Depot breaches) Read More...
|
Over 42 million cyber security incidents were reported in 2014...
According to a PWC survey, security incidents rose by 48% from 2013. This is not fear-mongering, and it's no time for anyone to be ignoring security. Read More... |
Tailored Security Awareness Assessment and Training Solutions to meet your organization's needs for compliance or risk reduction.
Whether you need customized webinars, live workshops, audio, videos or instructional CBT content, Security Perspectives Inc.'s Streetwise Security Awareness Tailored Assessment and Training programs can help you deploy a solution quickly and economically. You can go from requirements, to pilot to full roll-out within weeks. We also have quiz modules and games that can provide self- assessment or auditable records for compliance.
Learn about Streetwise Security Awareness Training
|
Stay Connected

|
| Security educators and entrepreneurs... |
I've got ideas and plans for creating new security assessment and education products for businesses and individuals. If you'd like to collaborate and get more things done faster, please contact me. We may be able to work together.
- Scott
|
|
 |
|
Greetings!
Welcome to Issue #6 of the Streetwise Security News.
On a personal note, it's cold here in Ottawa. So, I'm moving a little slower these days (average February temperature this year: -21 Celsius, or -5 degrees Fahrenheit). But it's a busy time, so time passes quickly.
I did a social engineering presentation in late January called "Fool Me Once: How Attackers Exploit Human Vulnerabilities" for the Ottawa chapter of the Information Systems Security Association. It was a lot of fun, and included a little magic and misdirection, to demonstrate how people can be distracted or tricked by an attacker.
Presenting for industry association events is something I like to do once in a while for no charge. I feel that the exposure to managers and executives from many organizations at one time is a win-win situation. So, I look forward to being invited to these kinds of sessions. Please let me know if you need a speaker for an event, and depending on my availability, I may be able to help you out (especially if it's in a warmer location than where I am now!).
See the list of topics on the left for a quick view of this issue's stories and content.
If you're not already a subscriber, and would like to sign up, please click HERE. You'll automatically receive a free copy of my Security Resource Guide that has links and source info for the tools I use on a daily basis. 
Cheers,
Scott Wright
|
 |

Only 31% of detected breaches were found by victim organizations. Who found the rest?
|
 When somebody tells the boss that an active data breach has been found in your network, wouldn't you like it to be somebody from your organization who found it? Well, that's not really happening very often.
According to the M-Trends report from Mandiant, only 31% of breach detection discoveries in 2014 were made by the victim organization. So, who else would be kind enough to make the effort to let your organization know it's been hacked?
The report from Mandiant identifies the FBI, as well as major credit card processors (i.e. Visa and Mastercard) as two important sources of external breach detection. Other external sources often include customers, suppliers, partners, security researchers and the attackers themselves. Most of these are not people you really want to hear this kind of news from... ever. There's a bit of good news in the report, in that the average time to detect a breach is down 10% in 2014 from 2013. However, the bad news is that this average is still 209 days. That means that an attacker can be inside your network, undetected, for over 6 months. If that's the case, shouldn't they also be entitled to an HR benefits package after the first 3 months?
One other thing to note is that, while this data is interesting, there's probably a lot we don't know about most data breaches. Determining how long an attacker has been inside your network - especially after a month or two - takes a lot of effort and specialized tools. If these tools aren't in place, it can be almost impossible to know exactly when an attacker got into the network.
We still have lots of work to do on detecting and responding to attacks on corporate networks. In the meantime, in addition to putting some kind of technology in place to help with detection, employees need to also be able to detect and report suspicious activity and incidents.
|
 Terminology - "Geolocation" Terminology - "Geolocation"
| |
Geolocation:
A technique for using GPS geographical positioning data
(usually together with a timestamp) from mobile devices to tag digital photos or social media posts. The embedded position data can often be used to determine an individual's location at a given date and time.
It's usually a good idea to turn of any
"location services" features on your mobile device, unless you need it for safety, navigation or searching.
You can find more information security terms and their definitions in the Streetwise Security Zone's Glossary. If you want to suggest a term to be added to the glossary or published in a future SSN issue, please send me a note at the coordinates below.
| |
 Scott's Recent Blog Posts Scott's Recent Blog Posts |
Here's a recent extract from my Security Views blog...
 Sometimes, we get confused about whom the enemy actually is. While businesses should be defending themselves against hackers and phishers, they often just want to get the auditors and regulators off their backs. Sometimes, we get confused about whom the enemy actually is. While businesses should be defending themselves against hackers and phishers, they often just want to get the auditors and regulators off their backs.
How can you tell whether you're fighting the wrong battle?
|
 Social Media Security Social Media Security |
|
Who's tweeting and Instagramming nearby? You can find some of them with Echosec
It's a little creepy, but there might be some good uses for a tool called Echosec. On the creepy side, you can zoom into a map view anywhere in the world, select an area on the map, choose a date range and see all the Twitter, Flickr and Instagram posts that can be traced to being posted within that geographic area (for now, it seems). The service takes advantage of geolocation information that can be found either within the images posted, or within the post's data itself.
Most mobile devices have the GPS location data available, and depending on your privacy settings or the permissions you give the apps on your device, that data may get posted.
I was surprised that there are so many  people who do not block their mobile apps from posting geolocation data. It's pretty easy to block on most devices, so people are either wanting their location data to be posted, or they don't care enough to block it, or they don't know it's being done when they post on their device. So, this is creepy enough that I would recommend most people block their location data using the location options on their mobile devices. If one setting controls access by all apps, I'd turn it off unless I really need the device to use my location - maybe to find a nearby bank machine or something important. Then turn it off immediately after.
There is a good reason to use this service, especially for corporate security enforcement. You may have a policy that people should not post from within the physical business location. You probably won't be able to detect people who have geolocation turned off on their devices, but you'll see those who don't bother. It can be a very useful tool for monitoring and educating staff (or family) about security and privacy.
Due to unforeseen circumstances, we weren't able to publish a Social Media Security Podcast episode this past month. But we hope to get back on track next month.
|
 Pinterest Pic of the Month
|
Use this on your home box [or wifi network] to keep your neighbors out of your internet > At least don't use your family name, pet's name or address!
|
 A Cyber Security Challenge Question A Cyber Security Challenge Question
|
 What feature of digital photos can cause unexpected exposure of your device's GPS and date/time information?: What feature of digital photos can cause unexpected exposure of your device's GPS and date/time information?:
a) Mobilocation
b) Photolocation
c) Coordination
d) Geolocation
Answer:
See the bottom of this newsletter for the answer. (or click HERE)
|
 Streetwise Security Tip - Don't blindly accept all privileges requested by mobile apps (they often don't need all of them) Streetwise Security Tip - Don't blindly accept all privileges requested by mobile apps (they often don't need all of them)
|
 |
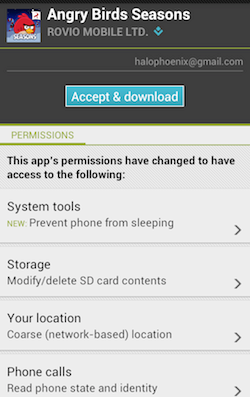 Most of us have probably downloaded at least one app to our mobile devices or phones by now. But have you ever noticed what they are asking for when you download them. Sometimes they don't need access to all the resources on your device that they are requesting. I recommend unchecking anything that doesn't seem like it's needed when the security screen appears. If they are asking for access to your contacts or documents, but the app is just a game that shouldn't need access to anything, you should start by unchecking them.
If the app really needs those things to work, it will tell you, either right away, or when you try to run it. This may sound like an inconvenience, but do you really want a game manufacturer to have access to all your contacts? I don't.
It's not always easy to figure out what the permission actually does, or why they need it. But it's easy to get into the habit of just accepting what's requested. I don't think this is a good idea, from a security point of view.
Most iPhones and iPads don't bother asking when you install an app, but the apps may ask for things like Location Services when you try to run them.
Android devices usually tell you what services an app wants permission to access.
My Blackberry also has a number of items that apps can request permission to access when they are downloaded. I uncheck any that don't make sense. Then if I get an error, it usually tells me what needs to be turned on for it to work.
This tip is also available for you to link to on my blog by clicking HERE.
|
 A Data breach story: It's much easier to rob a bank when the bank robbers can sit and watch bank employees doing transactions with keyloggers A Data breach story: It's much easier to rob a bank when the bank robbers can sit and watch bank employees doing transactions with keyloggers
|
 In late 2014, a new cyber-crime spree was uncovered that takes bank robbery to a whole new level. They stole money directly from as many as 100 banks over a 2 year period. Some reports say they were able to steal almost 1 billion dollars US during that time.
The Carbanak gang, as they are now known (also called Anunak - don't ask me where they come up with names for viruses and hacker groups...) developed a sophisticated method that all started with some simple phishing email messages that were sent to bank employees.
The basic idea was that, once the attachments in the phishing messages were opened, the employee's computers became infected with a keylogger (which you know, from reading past SSN issues, is a piece of malware that can send what you type and what's on your screen back to the attacker over the Internet).
It doesn't look like the attacks were based on exploiting any specific software or systems within the banks networks. The key to their success (for a period of months or years, anyway) was to use the keyloggers to watch what bank employees did to conduct transactions.
Once they learned system locations, account names and passwords, they were apparently able to transfer money between accounts, as well as dispense cash to ATMs without any local interaction at the machines. Each attack was a little different; so it took a long time to catch these guys. If you think about it, this kind of attack can be carried out against any kind of business. Banks just happened to be the easiest way for these guys to get cash. But attackers can make almost any kind of attack work if they can watch your employees doing their daily tasks. That's why keyloggers are so dangerous.
The bottom line here is that phishing is still (and probably will be for a long time) one of the most effective attack methods used by attackers. Put phishing together with a keylogger or botnet, and the game is almost over.
Please make sure your employees are trained on how to handle phishing attacks. Any kind of suspicious email that doesn't fit their normal business process should be treated with care. Employees need to spend time discussing these kinds of attacks and how they might appear in your organization. You can read more about the Carbanak attacks HERE. |
Answer to the Cyber Security Challenge Question (from above)
|
 Question - What feature of digital photos can cause unexpected exposure of your device's GPS and date/time information?:: Question - What feature of digital photos can cause unexpected exposure of your device's GPS and date/time information?::
Answer: (d) Geolocation. If you don't disable it, this feature of most mobile devices will automatically embed the device's GPS and date/time information into images you post and apps you are using. This can let tools like Echosec easily show strangers where you were, what you were posting, and more.
|
If you found this newsletter to be useful, I invite you to share it with one or two other associates or friends. If you have any comments, or even suggestions for stories you'd like to see in the next issue, please send me a note. In particular, I'd love to hear which stories you enjoyed the most, and what you'd like to see more of. Sincerely, Scott Wright
The Streetwise Security Coach Security Perspectives Inc.
|
|
|